
Hackers can turn Google Calendar into a malware management tool
Google has uncovered a fresh security threat within its "Google Calendar" service: hackers can potentially employ it to manage malicious software by concealing commands within ordinary calendar entries. Such actions can be challenging to detect, creating significant cybersecurity risks. Intriguingly, Google itself warns that "Calendar" could be used for surreptitious command transmission to malicious software.
Many viruses, once infiltrating a victim's system, require external control from malicious actors. This necessitates the creation of a specialized "Command and Control" infrastructure (C2). Typically, hackers dispatch commands to their malicious software via a so-called C2 server. However, they have now discovered a means to mask their activity by utilizing legitimate services like cloud storage and email systems.
In the past, hackers have already utilized services such as Dropbox, Amazon Web Services, Google Drive, and Gmail for similar purposes. This allowed them to cloak commands to viruses as regular internet traffic, making detection a challenge for antivirus programs and cybersecurity experts.
Google is currently highlighting the potential danger in using "Calendar" as a novel tool for C2 communications. In their report on future threats, the company references a cybersecurity study where an expert using the pseudonym MrSaighnal demonstrates the methodology of using "Google Calendar" for malicious purposes.
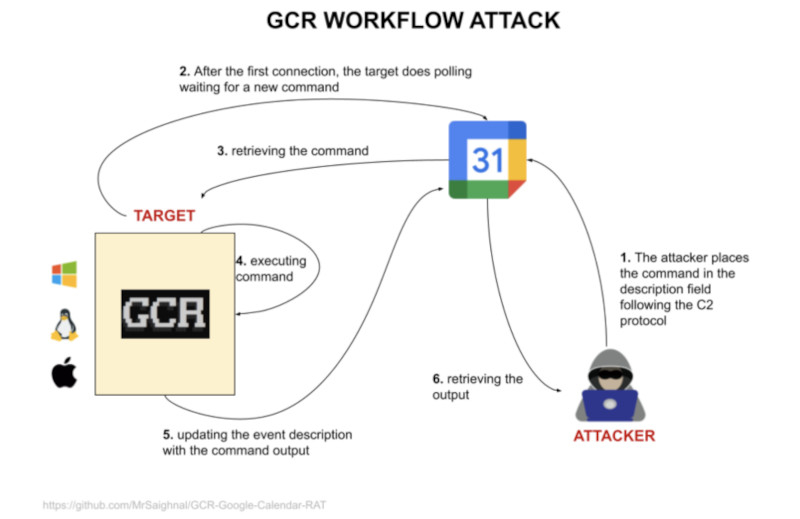
The methodology, referred to as Google Calendar RAT (GCR), involves placing C2 commands in event descriptions on the calendar. Malicious software installed by hackers can routinely check the "Google Calendar" account for new commands and execute them on an infected device.
According to the developer, GCR exclusively interacts through legitimate infrastructure managed by Google, making it difficult for defenders to detect suspicious activities.
The discovery of this vulnerability in "Google Calendar" raises new questions about the security of seemingly dependable digital services. It also underscores the necessity of consistently updating cybersecurity practices and closely monitoring any changes in software behavior.
- Related News
- Which smartphones will be the first to receive Android 15?
- Android smartphone users can now send emojis during phone calls
- Compact, great cameras and low price: What do we know about the Google Pixel 8a?
- Alphabet will pay dividends for the first time in its history
- Google's Gemini app is already available for older versions of Android
- Google is developing a budget smartwatch
- Most read
month
week
day
- Xiaomi unveils exclusive Redmi Note 13 Pro+ dedicated to Messi and Argentina national team 972
- Internet 500 times faster than 5G tested in Japan: It allows to transfer five movies in HD resolution in one second 823
- What will happen to the Earth if the Moon disappears? 740
- Which smartphones will be the first to receive Android 15? 739
- iPhone 16 may get colored matte glass back panel, 7 colors 717
- Great value for money: 3 best Realme smartphones 705
- WhatsApp receives two new features 670
- Why it is recommended to download applications on trusted platforms: In 2023, Google rejected publication of more than 2 million dangerous applications on Google Play 614
- Instagram is changing its approach to content recommendations: How will the application help promote original content and fight reposters? 585
- How to realize that your smartphone is hacked and you are being surveilled? 557
- Archive
