
What is MFA fatigue and how do attackers try to steal accounts using it?
Attackers often use so-called social engineering techniques to gain access to accounts and to break into large networks. A technique called MFA Fatigue (MFA) is one element of such attacks, and it has become increasingly popular among hackers lately.
When hacking corporate networks, attackers usually use stolen employee credentials to gain access to VPNs and internal networks. Getting this data is not as difficult as the uninformed might think: hackers use phishing attacks, malware, and leaked credentials due to vulnerabilities in the system or through purchases on Darknet marketplaces.
To protect the corporate network, many self-respecting companies implement multi-factor authentication (MFA) so that users cannot log onto the network without an additional form of verification, which can be a one-time access code, a login confirmation request, etc.
Hackers can use a variety of methods to bypass multifactor authentication: most involve stealing cookies through malware or phishing tools.
However, lately, as mentioned above, the MFA fatigue method is becoming increasingly popular, because it requires neither malware nor phishing infrastructure, and the effectiveness of the method is quite high.
What is MFA fatigue?
According to Bleepingcomputer.com, if an organization sets up multifactor authentication to send push notifications, an employee receives notifications on their mobile device that someone is trying to log into the network with their credentials. The employee can either confirm or deny the login (see screenshot below).
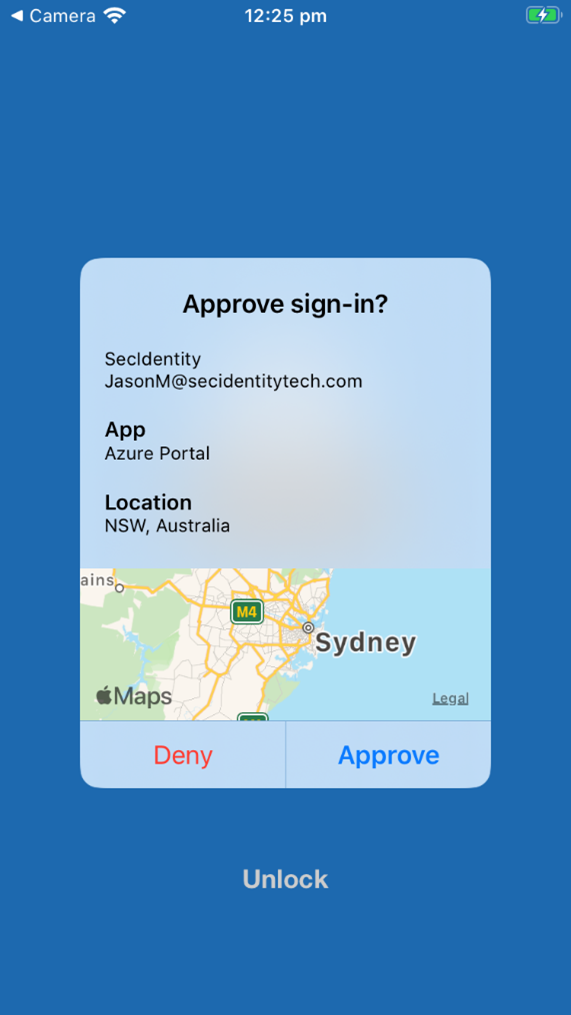
In the MFA fatigue attack, an attacker runs a script that repeatedly tries to connect to the network using compromised usernames and passwords.
As a result, an endless number of notifications are sent to the employee's mobile device.
The goal of the attackers is to make the victim tired of the notifications coming day and night and to dull his vigilance about cybersecurity. You can see a clear demonstration of this technique in the video:
In many cases, attackers send repeated MFA notifications and then contact the potential victim via email, messenger, or phone, impersonate support staff and try to convince the user to accept the MFA request. Tired of the constant notifications, the victim may accidentally press the 'confirm' button or simply accept the request to stop the stream of notifications s/he was receiving on his/her phone. This is the method hackers Lapsus$ and Yanluowang used to hack Microsoft, Cisco, as well as Uber.
What to do if you are attacked using MFA Fatigue?
If you are the victim of an MFA Fatigue attack and are receiving a barrage of MFA push notifications:
- Don't panic!
- Never confirm an MFA request in the hope of stopping the flood of notifications!
- Don't talk to strangers claiming to be from your organization or representing customer service!
What should you do then?
- The first thing to do is contact your company's IT administrators or your managers and explain the situation.
- Change the password for your account so that the hacker cannot continue to log in and generate further MFA push notifications.
- Once your password is changed, the hacker will no longer be able to send out MFA spam, allowing you and administrators to begin quietly investigating the situation to understand how and when your data was compromised.
To improve corporate network security, experts recommend disabling MFA push notifications, or if you cannot do that, you can enable number matching to improve security.
You can also limit the number of authentication requests per user, and if the limit is exceeded, block accounts and notify the administrator.
Some experts suggest that enterprises switch to hardware security keys to protect logins, but the problem is that such keys may not be compatible with some online services.
- Related News
- What risks are hidden in keyboards of Android smartphones?
- Hackers attack more than 19 million Russians with Android smartphones
- iPhone users are advised to disable iMessage: What risks are hidden in it?
- Why it might not be a good idea to close background apps on Android?
- What signs can indicate presence of malicious applications in your smartphone?
- How to recognize fake documents on the Internet?
- Most read
month
week
day
- 10 most interesting architectural works of Zaha Hadid 747
- How will new technologies change future of finance? Interview with director of Apricot Capital (video) 745
- 5 original buildings with curious optical illusions (photos) 740
- What risks do crypto and digital currencies pose? Interview with Rasmus Nielsen 706
- 4 flares erupted from Sun in rare event: the Earth may be hit by geomagnetic storm (video) 632
- Google is developing a budget smartwatch 627
- Alphabet will pay dividends for the first time in its history 626
- Date of new Apple presentation known: When will they show us new iPad Pro with OLED screen? 618
- Large taxpayers of Armenia’s IT sector: What changes have taken place in 2024 Q1? 613
- Android 15 to get two useful new features 612
- Archive
